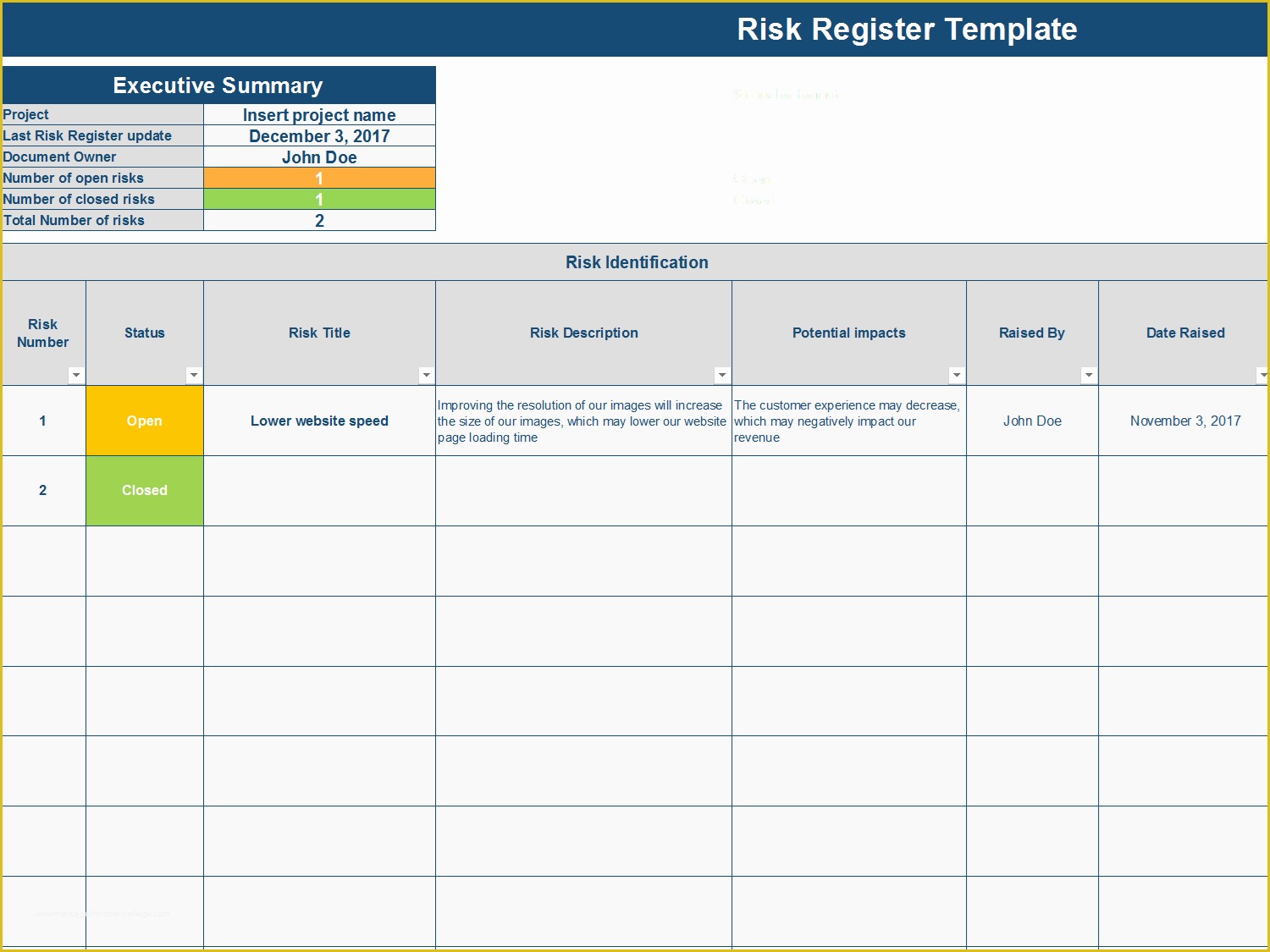
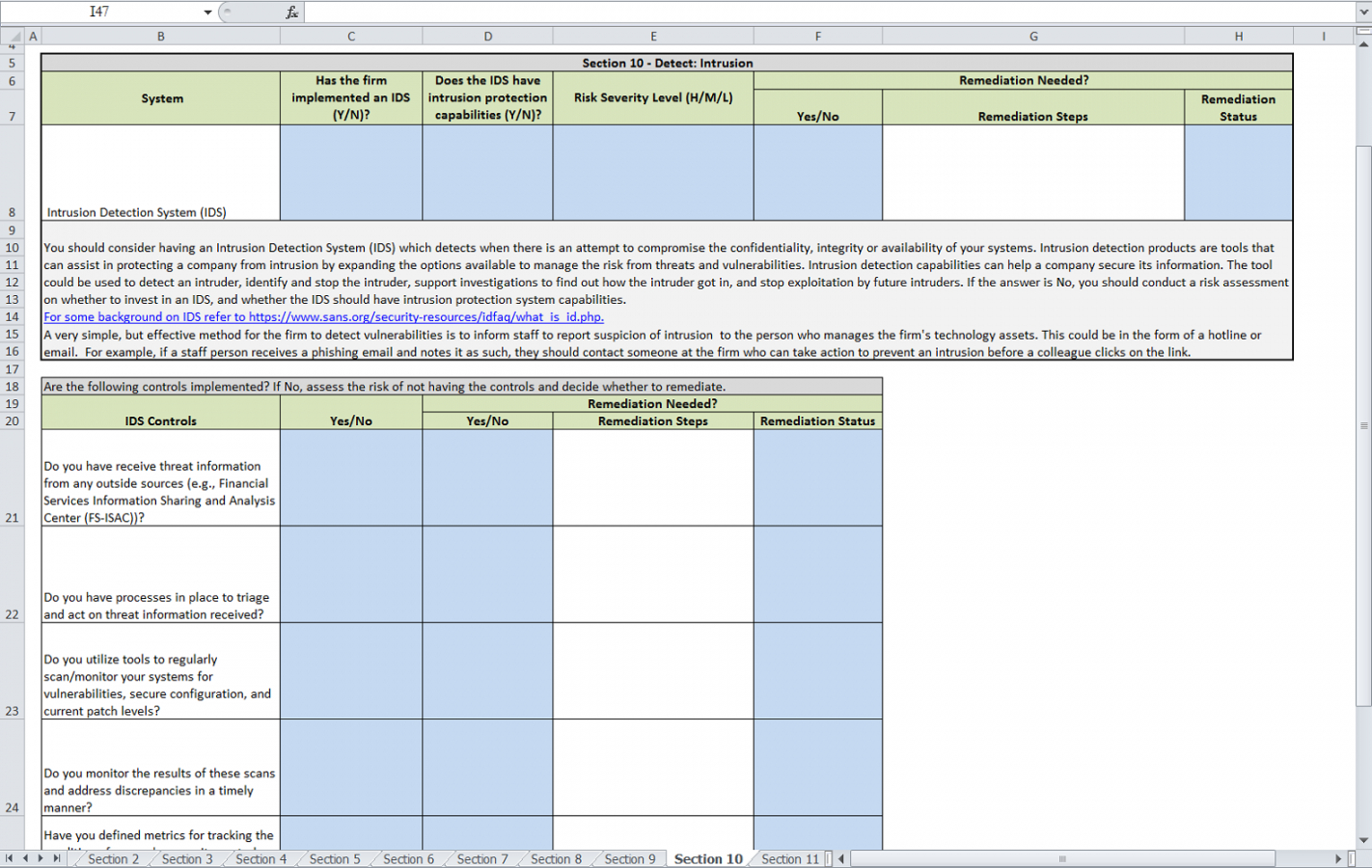
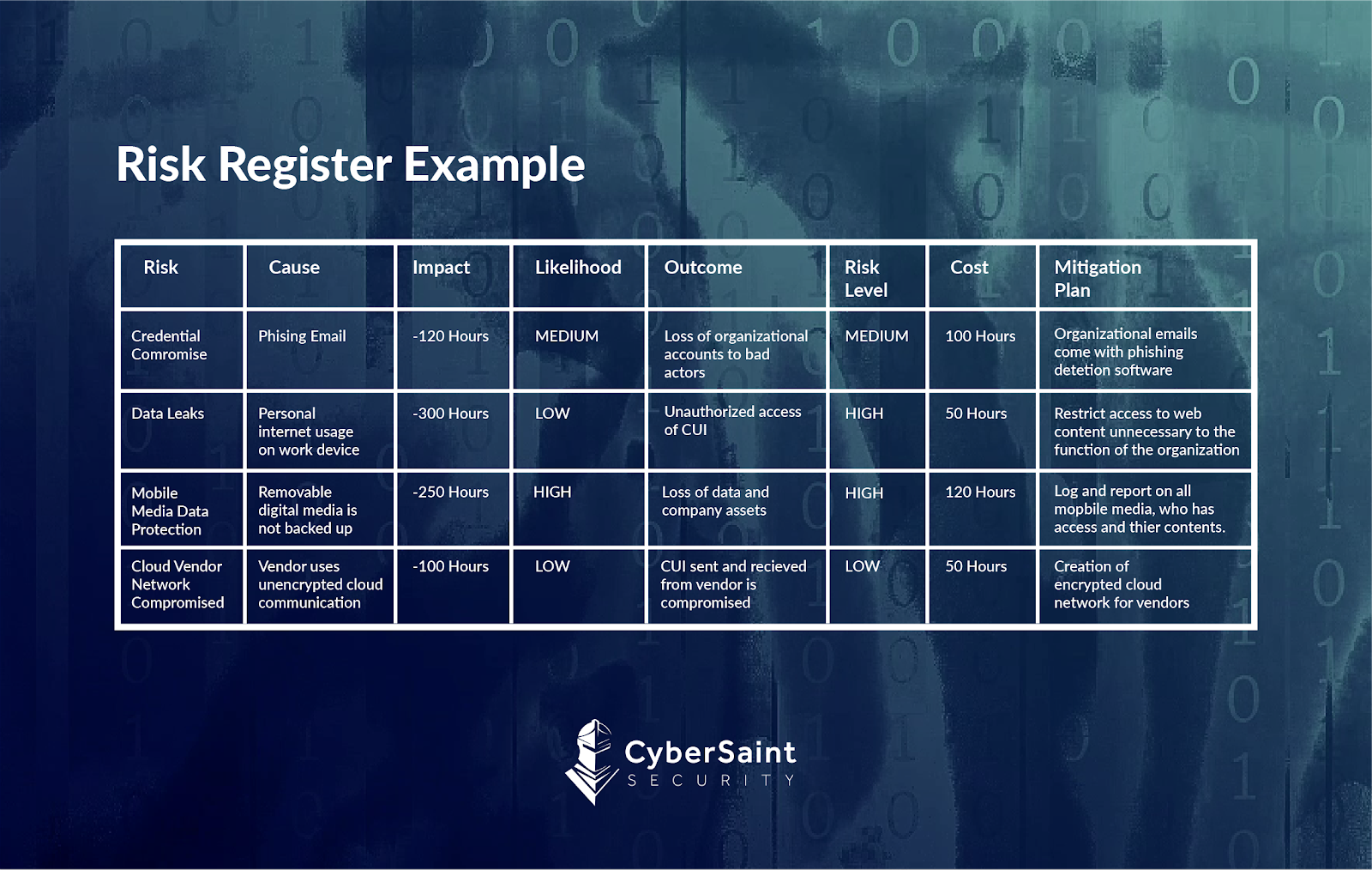
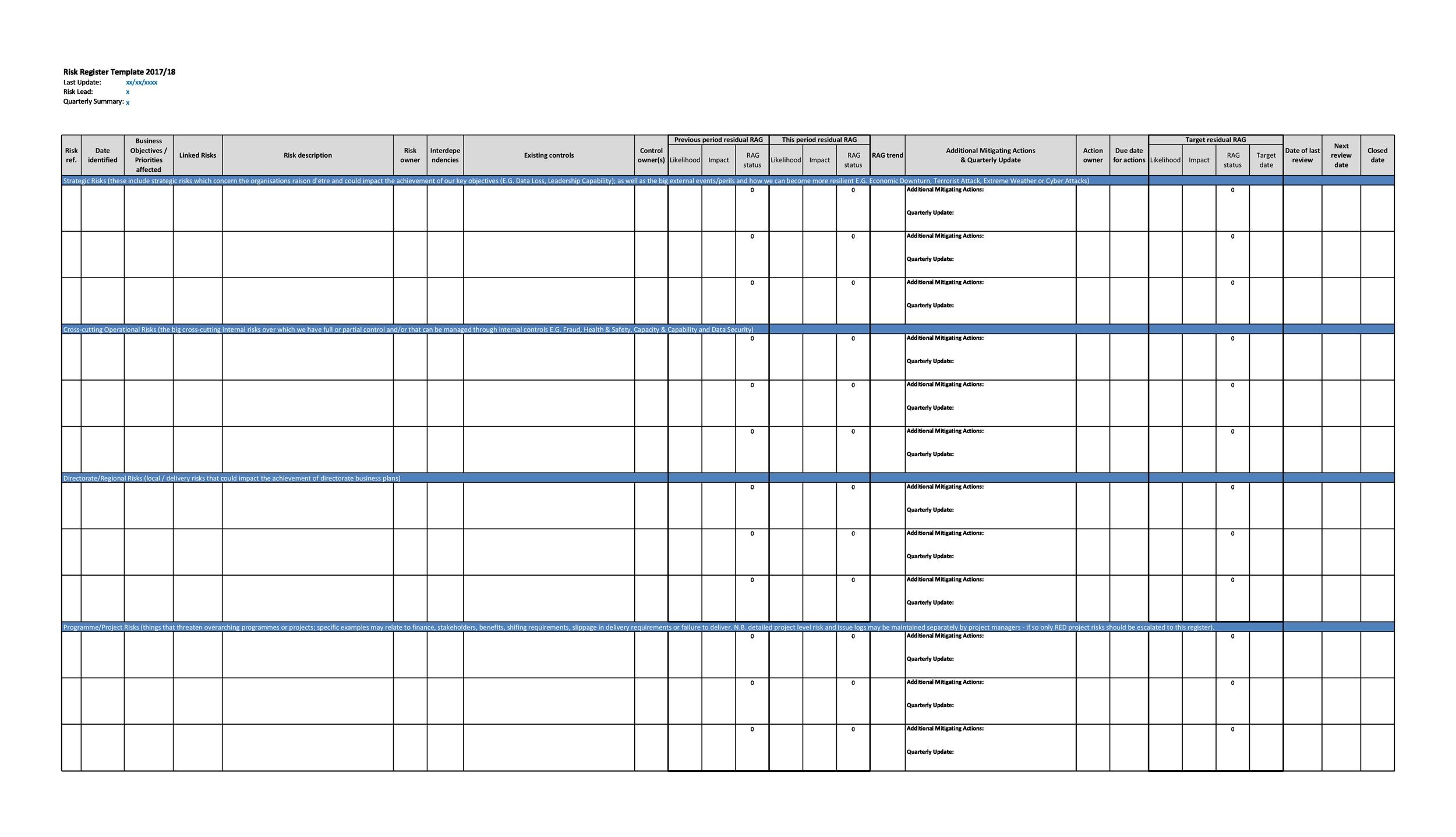
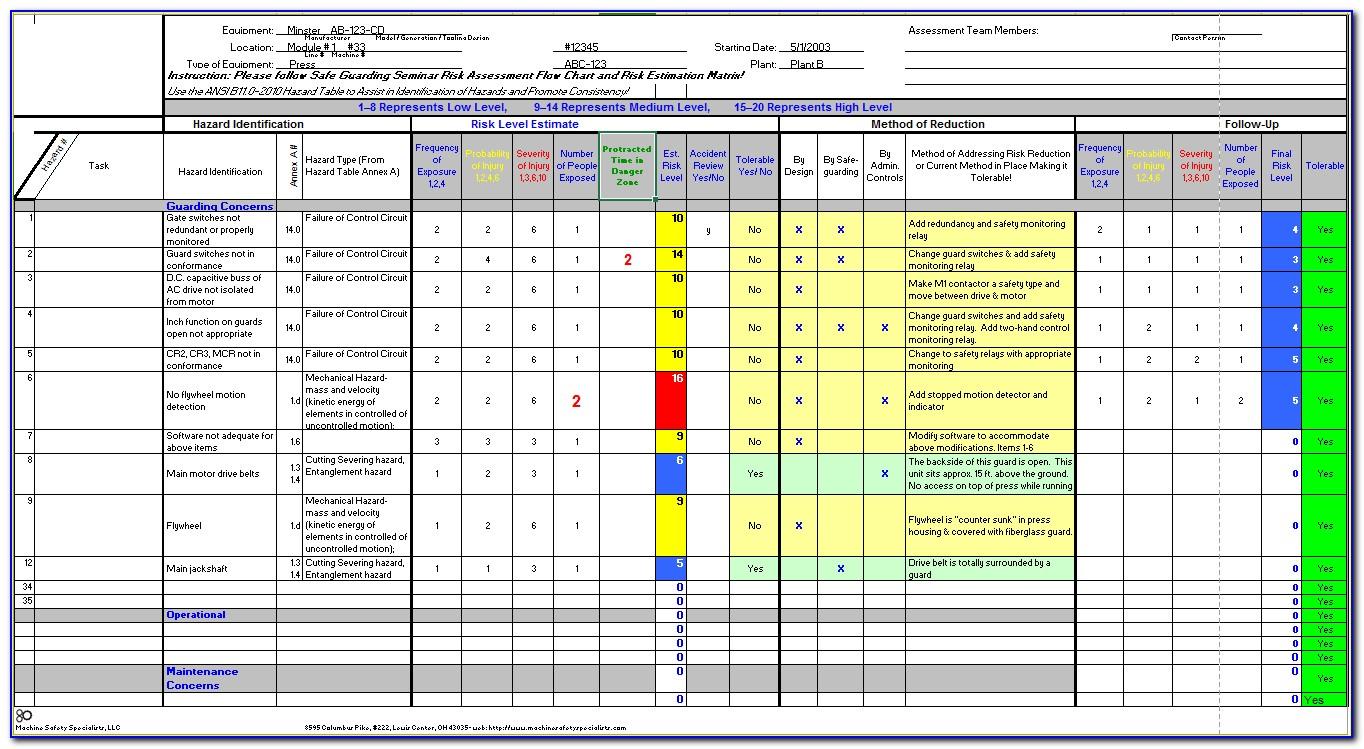
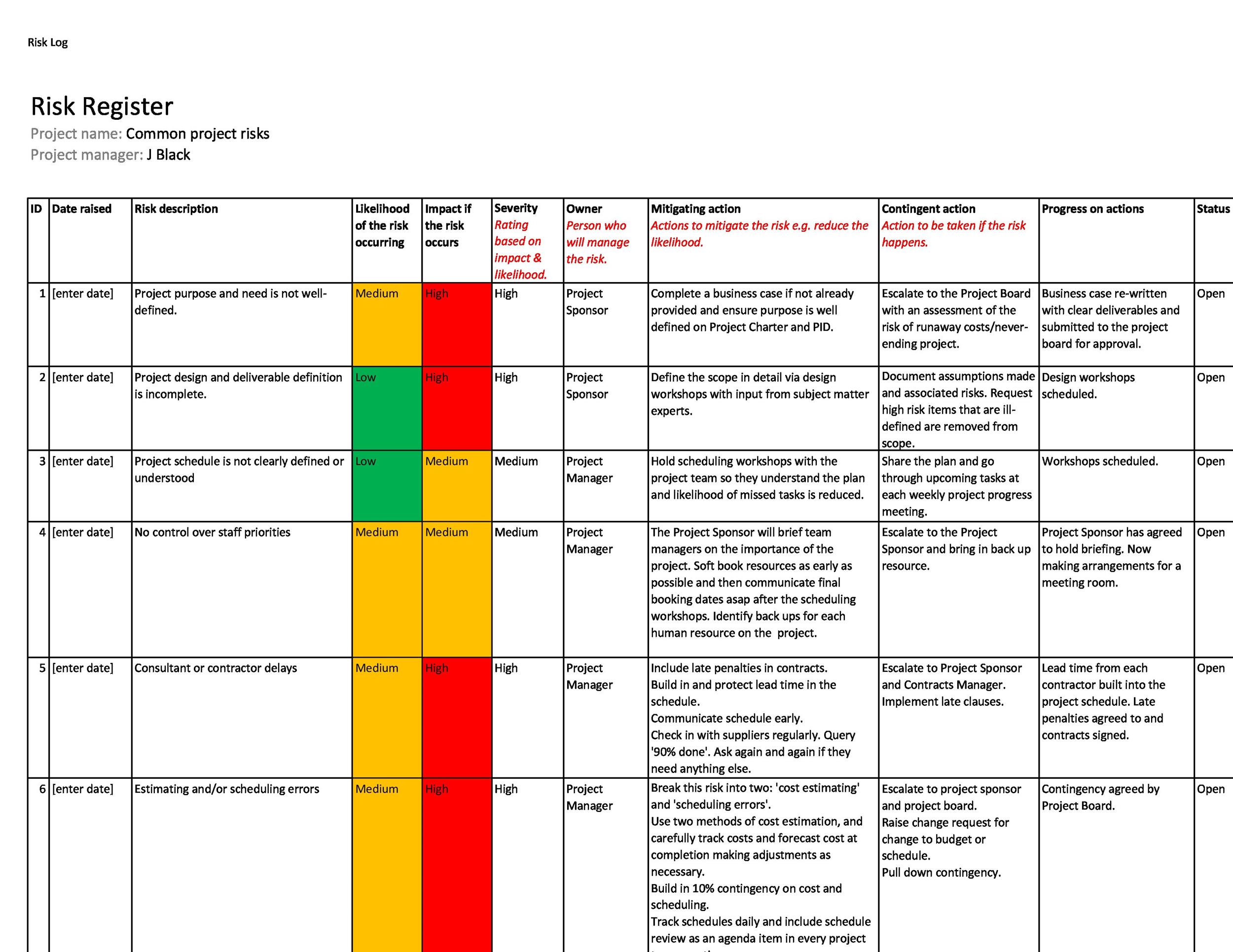
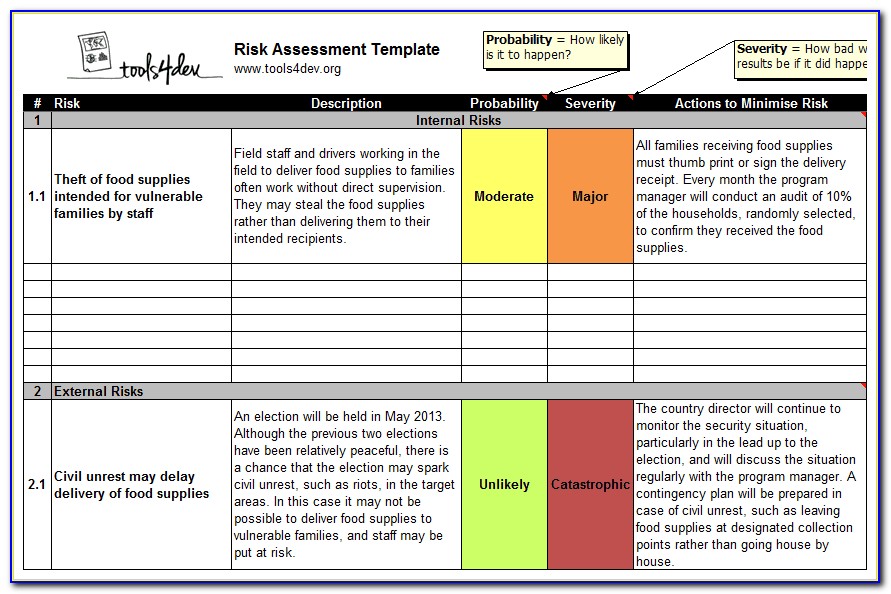
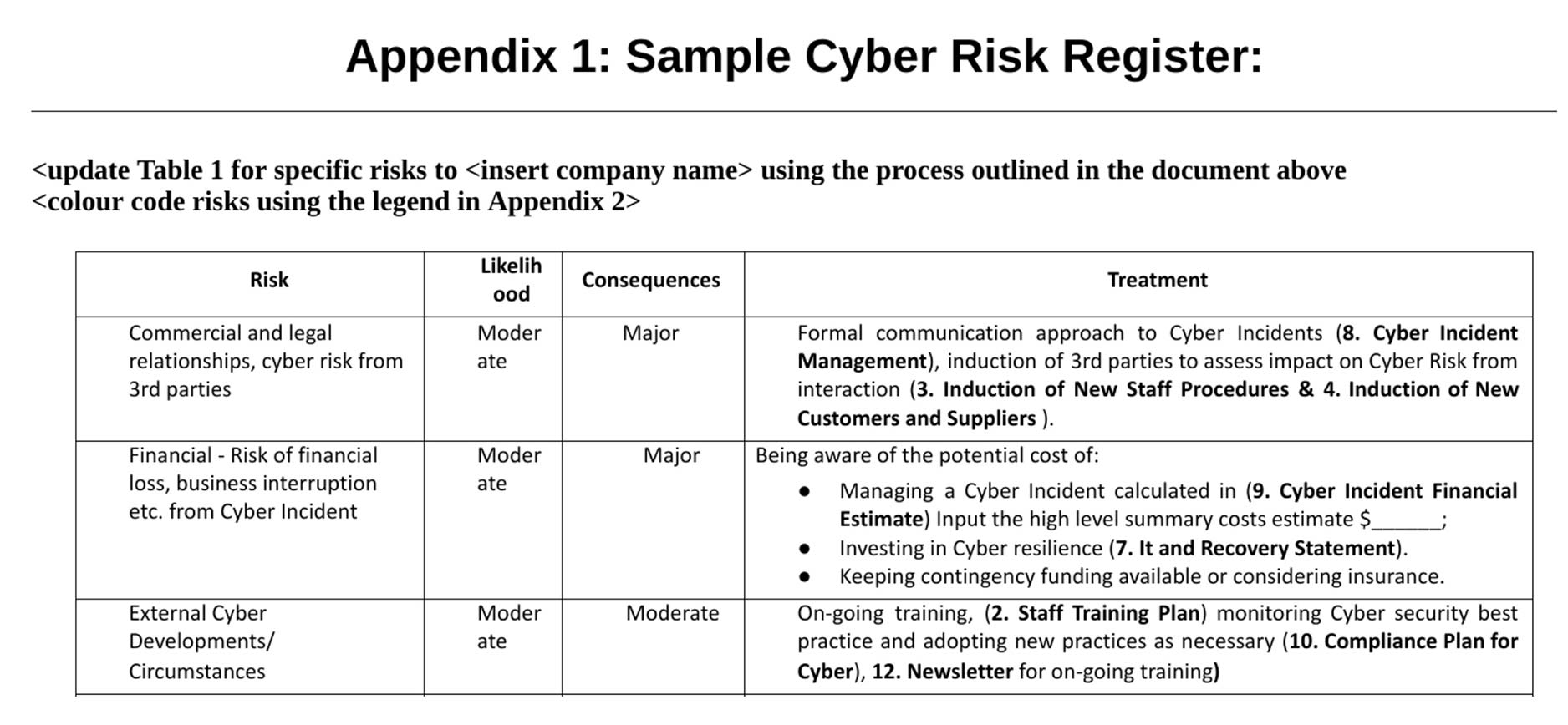
Cyber Risk Register Template
Cyber Risk Register Template - Linking controls to “best practice”. Current risks are comprised of both accepted risks and risk. Putting solid security in place is key to getting the coverage you need. Web your risk framework needs to map to internal and external gaps to identify weaknesses and ensure complete coverage. Web crafting a risk register ‘power tool’ as the base for a multiyear cybersecurity plan; The case for using multiple risk registers. It’s a starting point for building out your own risk register. Similar processes, and the general use of risk registers, are helpful to. The michigan department of technology, management & budget’s client service center (csc) serves as the primary point of contact for state of. Web cybersecurity risk assessment templates let’s take a look at the cis critical security controls, the national institute of standards and technology (nist).
48 Cyber Security Powerpoint Template Free Heritagechristiancollege
In this webinar, you will learn how to: You can download our free risk register template for excel. Web examples of risk registers for cybersecurity leaders. Resources include, but are not limited to: A central record of current risks, and related information, for a given scope or organization.
Cybersecurity Risk Assessment Template for creating cybersecurity
This is a listing of publicly available framework resources. A central record of current risks, and related information, for a given scope or organization. Web cyber risk reporting template tags: Current risks are comprised of both accepted risks and risk. With many moving parts to handle,.
Risk Assessment Template Excel Classles Democracy
Current risks are comprised of both accepted risks and risk. This is a listing of publicly available framework resources. Web august 21, 2023. Creating a register might seem easy using a generic project plan risk register template found online, but properly. Ad what do insurers look for when they approve and price cyber insurance coverage?
Risk Register Examples for Cybersecurity Leaders
Web august 21, 2023. Web risk register definition (s): Getapp has helped more than 1.8 million businesses find the best software for their needs. Web cybersecurity risk assessment templates let’s take a look at the cis critical security controls, the national institute of standards and technology (nist). Web cyber risk reporting template tags:
Risk Assessment Risk Register Template Excel Construction Risk
Web of leaders cannot see the full spectrum of online threats against their businesses. Web crafting a risk register ‘power tool’ as the base for a multiyear cybersecurity plan; Risk management reporting on your cyber risk posture to your board can be daunting. It’s a starting point for building out your own risk register. Web august 21, 2023.
Nist Risk Assessment Template Xls
Web nist privacy risk assessment methodology (pram) the pram is a tool that applies the risk model from nistir 8062 and helps organizations analyze, assess,. In hyperproof, organizations can set up multiple risk registers to track different types of risks and customize the scales/risk scoring for each risk register. How can risk join help? This is a listing of publicly.
Cyber Crime Risk Assessment Adam M. Erickson
Putting solid security in place is key to getting the coverage you need. Risk management reporting on your cyber risk posture to your board can be daunting. Web nist privacy risk assessment methodology (pram) the pram is a tool that applies the risk model from nistir 8062 and helps organizations analyze, assess,. The case for using multiple risk registers. You.
45 Useful Risk Register Templates (Word & Excel) ᐅ TemplateLab
With many moving parts to handle,. It’s a starting point for building out your own risk register. Web risk register definition (s): A central record of current risks, and related information, for a given scope or organization. Current risks are comprised of both accepted risks and risk.
Example Cybersecurity Risk Assessment Matrix Nist 800 37 Risk
Web overview more than ever, organizations must balance a rapidly evolving cybersecurity and privacy threat landscape against the need to fulfill business requirements on an. Web cybersecurity risk assessment templates let’s take a look at the cis critical security controls, the national institute of standards and technology (nist). Risk management reporting on your cyber risk posture to your board can.
Cyber Procedures to Tailor and Implement Pink Cyber Cyber security
The michigan department of technology, management & budget’s client service center (csc) serves as the primary point of contact for state of. Linking controls to “best practice”. Current risks are comprised of both accepted risks and risk. Web crafting a risk register ‘power tool’ as the base for a multiyear cybersecurity plan; In this webinar, you will learn how to:
The case for using multiple risk registers. Web cybersecurity risk assessment templates let’s take a look at the cis critical security controls, the national institute of standards and technology (nist). A central record of current risks, and related information, for a given scope or organization. Web crafting a risk register ‘power tool’ as the base for a multiyear cybersecurity plan; You can download our free risk register template for excel. Web examples of risk registers for cybersecurity leaders. Linking controls to “best practice”. Creating a register might seem easy using a generic project plan risk register template found online, but properly. Web of leaders cannot see the full spectrum of online threats against their businesses. Ad what do insurers look for when they approve and price cyber insurance coverage? Similar processes, and the general use of risk registers, are helpful to. Getapp has helped more than 1.8 million businesses find the best software for their needs. How can risk join help? In hyperproof, organizations can set up multiple risk registers to track different types of risks and customize the scales/risk scoring for each risk register. Web risk register definition (s): Current risks are comprised of both accepted risks and risk. The michigan department of technology, management & budget’s client service center (csc) serves as the primary point of contact for state of. In this webinar, you will learn how to: With many moving parts to handle,. Putting solid security in place is key to getting the coverage you need.