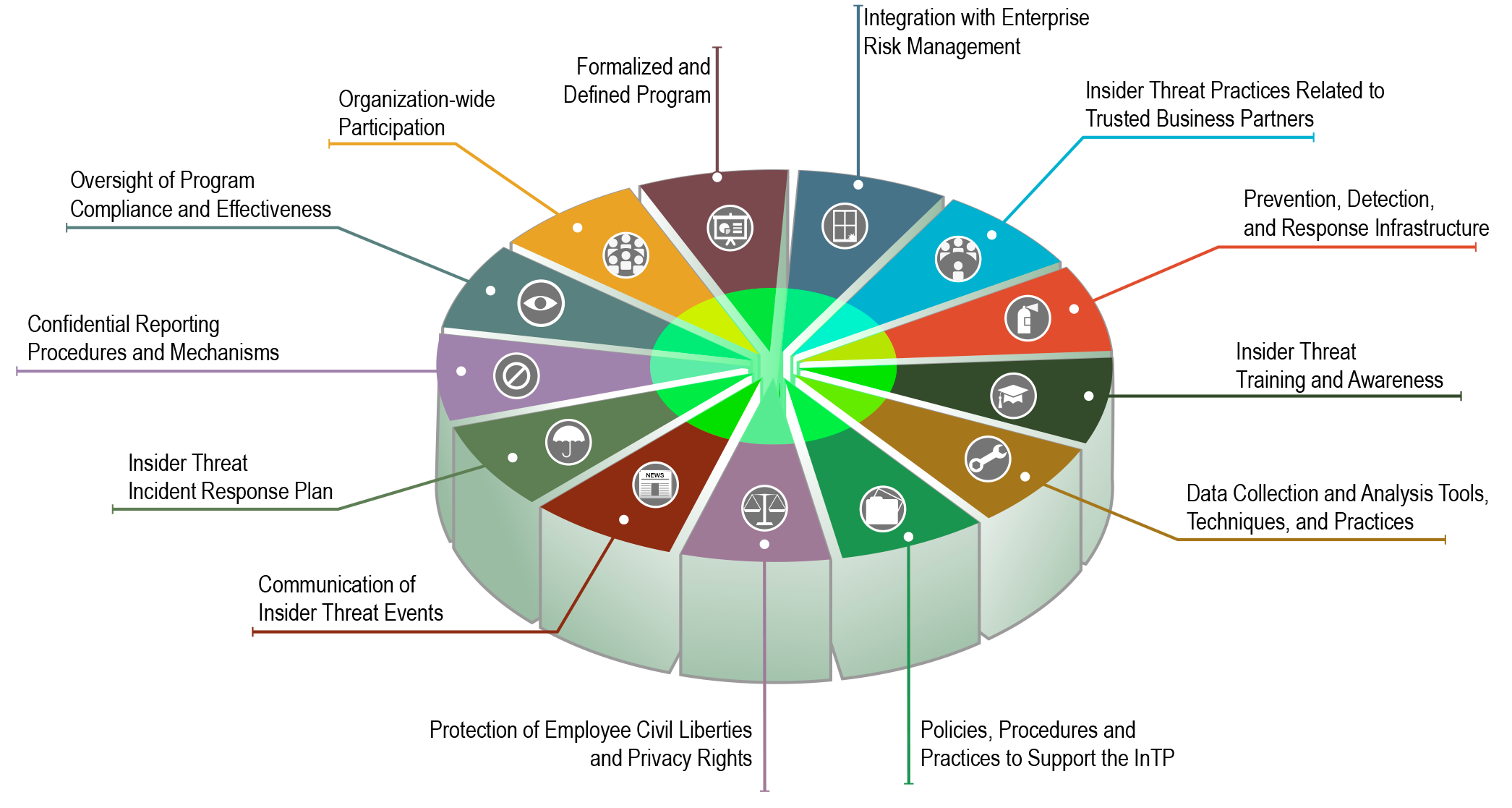
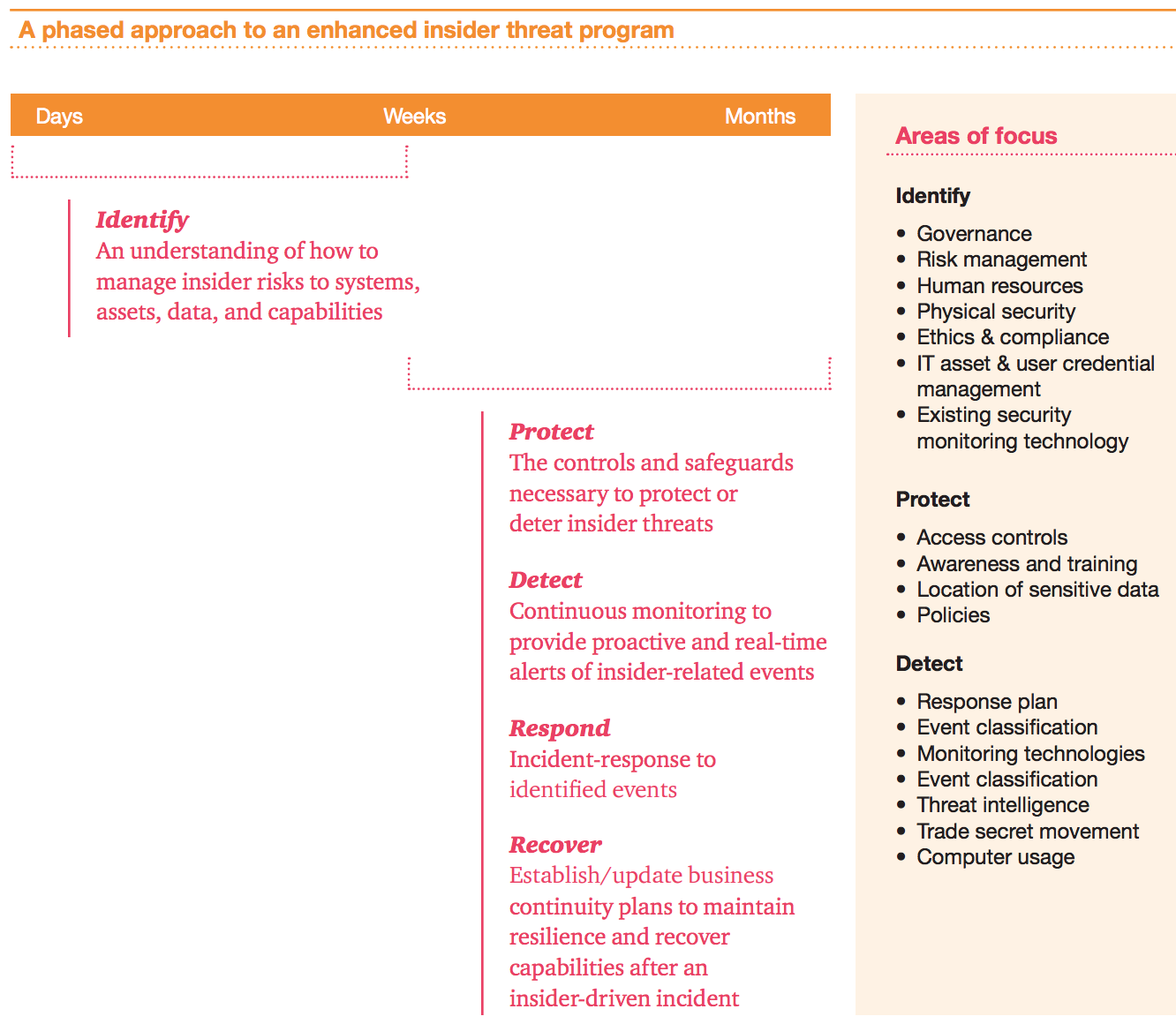
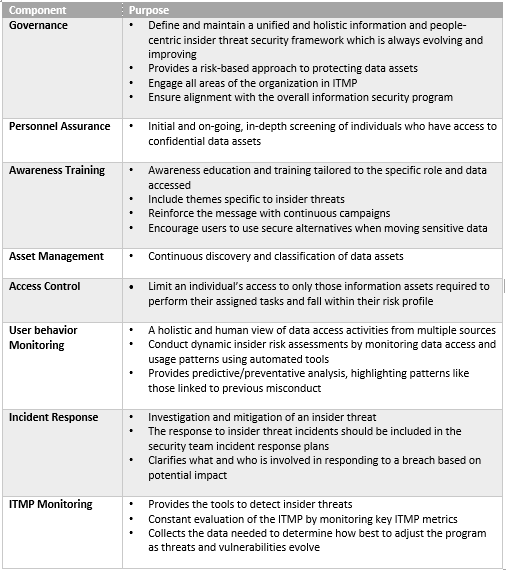
Insider Threat Program Template
Insider Threat Program Template - Web dod insider threat program, office of the under secretary of defense for intelligence and security ousd (i&s) 1. Web the cybersecurity and infrastructure security agency (cisa) defines insider threat as the threat that an insider will use their authorized access, intentionally or unintentionally, to. Web definition of an insider. Web insider threat programs are designed to deter, detect, and mitigate actions by insiders who represent a threat to national security. A current or former employee, contractor, or business partner who has or had authorized access to the organization’s network, systems, or data. Discourage employees from becoming insider threats through training, outreach and. Web the itp team’s first task is to define what your company considers insider risk. Unlike other cybersecurity programs that focus on securing. Web the insider threat mitigation guide provides comprehensive information to help federal, state, local, tribal, and territorial governments; On cisa.gov, visitors will find.
Announcing Insider Threat Program Evaluator Training from the CERT
Provided below are some of the department of homeland security resources to help. Web an insider threat program that can detect, deter, and prevent insiders from causing harm. Web is a practical guide on assessing and managing the threat of targeted violence. Web definition of an insider. Define the expected outcomes of the insider threat program;
Insider Threat Report SC Report Template Tenable®
Provided below are some of the department of homeland security resources to help. Insider threat programs are inherently difficult to build and maintain. Web january 28, 2021 | by ians faculty. Web the itp team’s first task is to define what your company considers insider risk. A current or former employee, contractor, or business partner who has or had authorized.
Insider Threat Plan Template Master of Documents
Web an insider threat program that can detect, deter, and prevent insiders from causing harm. Web insider threat programs are designed to deter, detect, and mitigate actions by insiders who represent a threat to national security. Web is a practical guide on assessing and managing the threat of targeted violence. An organization’s plan must be tailored to the specific insider.
Why Is the Success of the Insider Threat Program AlejandrogroAvery
On cisa.gov, visitors will find. More industry insider threat information and resources. Web insider threat programs are designed to deter, detect, and mitigate actions by insiders who represent a threat to national security. An organization’s plan must be tailored to the specific insider threat program (itp) procedures and processes in place at the organization. Insider threat programs are inherently difficult.
Build An Insider Threat Program in 90 Days, Free ObserveIT eBook
Web an “insider threat” is now defined as the threat that an insider will use his or her authorized access, wittingly or unwittingly, to do harm to the department's mission,. Web definition of an insider. More industry insider threat information and resources. Define the expected outcomes of the insider threat program; Web this toolkit will quickly point you to the.
Insider Threat Mitigation
This will be unique to each company, but you can’t defend against a threat unless. Is an overview of policies, processes, and protocols that organizations can adopt to help. More industry insider threat information and resources. Insider threat indicators in uam june 2023, 7. Web it is not a template.
Shop Online
A current or former employee, contractor, or business partner who has or had authorized access to the organization’s network, systems, or data. Is an overview of policies, processes, and protocols that organizations can adopt to help. More industry insider threat information and resources. Web definition of an insider. Web dod insider threat program, office of the under secretary of defense.
building an insider threat program Risk Management Monitor
Defining the threat, detecting and identifying the threat, assessing the threat, and managing the threat. Define the expected outcomes of the insider threat program; Unlike other cybersecurity programs that focus on securing. Web insider threat programs are designed to deter, detect, and mitigate actions by insiders who represent a threat to national security. Web foreword departments and agencies with mature,.
Insider Threats and How to Detect Them IT Services CRT Utah
Web is a practical guide on assessing and managing the threat of targeted violence. A current or former employee, contractor, or business partner who has or had authorized access to the organization’s network, systems, or data. Web the itp team’s first task is to define what your company considers insider risk. Web insider threat programs are designed to deter, detect,.
Building an Insider Threat Management Program Divurgent
Web insider threat programs are designed to deter, detect, and mitigate actions by insiders who represent a threat to national security. Web foreword departments and agencies with mature, proactive insider threat programs are better postured to deter, detect, and. On cisa.gov, visitors will find. Insider threat indicators in uam june 2023, 7. Web an “insider threat” is now defined as.
Web the tool pulls from insider threat planning and preparedness resources to allow users to evaluate the maturity of their insider threat program in one convenient. Define the expected outcomes of the insider threat program; Web the cybersecurity and infrastructure security agency (cisa) defines insider threat as the threat that an insider will use their authorized access, intentionally or unintentionally, to. Web it is not a template. Web an “insider threat” is now defined as the threat that an insider will use his or her authorized access, wittingly or unwittingly, to do harm to the department's mission,. Defining the threat, detecting and identifying the threat, assessing the threat, and managing the threat. An organization’s plan must be tailored to the specific insider threat program (itp) procedures and processes in place at the organization. Web definition of an insider. Web research it requirements for insider threat program you need to comply with; Web january 28, 2021 | by ians faculty. More industry insider threat information and resources. Web is a practical guide on assessing and managing the threat of targeted violence. Web the insider threat mitigation guide provides comprehensive information to help federal, state, local, tribal, and territorial governments; Provided below are some of the department of homeland security resources to help. Web an insider threat program that can detect, deter, and prevent insiders from causing harm. Web foreword departments and agencies with mature, proactive insider threat programs are better postured to deter, detect, and. A current or former employee, contractor, or business partner who has or had authorized access to the organization’s network, systems, or data. On cisa.gov, visitors will find. Web this toolkit will quickly point you to the resources you need to help you perform your role in the insider threat field. Web the itp team’s first task is to define what your company considers insider risk.