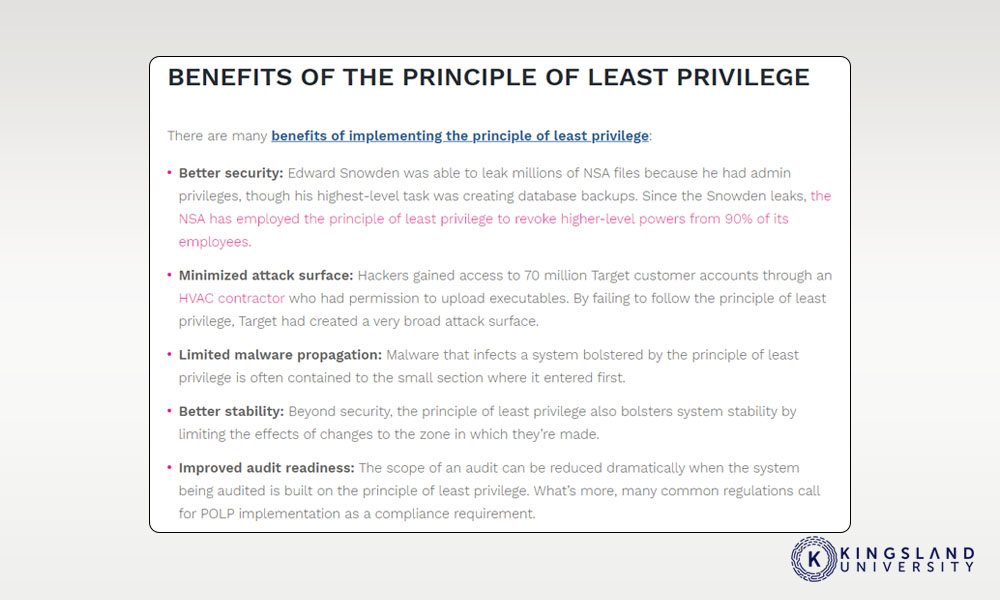
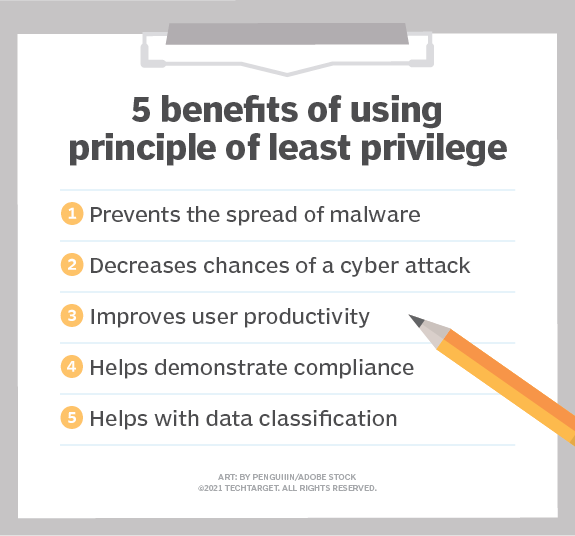
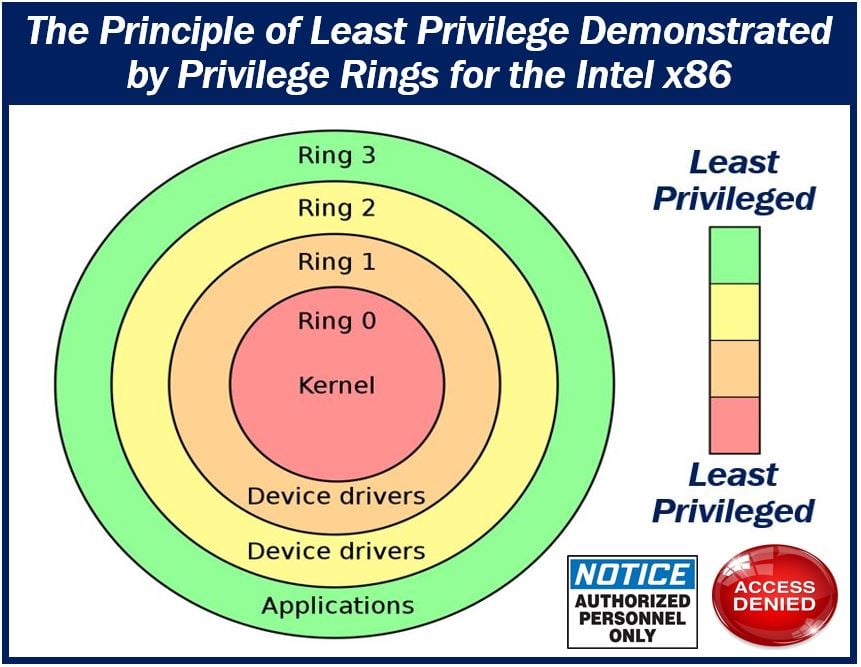
Least Privilege Policy Template
Least Privilege Policy Template - Web follow the principle of least privilege to implement a zero trust security strategy never grant broad or standing privileges. Best practice guide to implementing. In this post, i’ve shown two different techniques that you can use to create least privilege policies for iam. They are based on compliance requirements outlined by cis, nist, pci and. Web the principle of least privilege model (also called the principle of minimal privilege or the principle of least authority) is widely considered to be a cybersecurity. Best practice guide to implementing the least. Web the principle states that all users should log on with a user account that has the absolute minimum permissions necessary to complete the current task and nothing. Web the principle of least privilege (polp) the first security principle that i am going to discuss is one that most system administrators are familiar with: Your organization should also focus on building and maintaining a specific set of policies for. Web a minimum access policy ensures that users have the lowest level of privileges to complete necessary functions.
8 Tips to Train Your Staff and Employees for Cybersecurity
Least privilege is the concept and practice of restricting. They are based on compliance requirements outlined by cis, nist, pci and. Web applying the principles of least privilege aws identity and access management (iam) is the service used to manage access to aws services. In a least privilege model, privileged users and systems have. In this post, i’ve shown two.
PPT Secure Software Development PowerPoint Presentation, free
Before using iam, it’s important to. In a least privilege model, privileged users and systems have. Instead, provide only the needed level of privilege to. Best practice guide to implementing. Privileged access users must have permissions set to the lowest level of access needed to accomplish their job function.
Enforcing principle of least privilege
Web the information security principle of least privilege asserts that users and applications should be granted access only to the data and operations they require to. Web follow the principle of least privilege to implement a zero trust security strategy never grant broad or standing privileges. The principle of least privilege access is a software security best practice that provides.
PPT Security Principles and Practice PowerPoint Presentation, free
Web applying the principles of least privilege aws identity and access management (iam) is the service used to manage access to aws services. What is the principle of least privilege (polp)? Web a minimum access policy ensures that users have the lowest level of privileges to complete necessary functions. Web the principle of least privilege model (also called the principle.
Principle of least privilege examples & best practices
Web applying the principles of least privilege aws identity and access management (iam) is the service used to manage access to aws services. One of the biggest advantages to a least. Web the principle of least privilege reduces risk by preventing people from having more access than they need. Web the principle states that all users should log on with.
PPT IS3340 Windows Security Unit 2 Setting up Windows Systems with
In a least privilege model, privileged users and systems have. Web the principle of least privilege model (also called the principle of minimal privilege or the principle of least authority) is widely considered to be a cybersecurity. Web 19 jan 2022. Scope these controls apply to information and information processing systems at the. Web this guide explains the principle out.
The 5 Most Important Strategies of the Security Principle of Least
Before using iam, it’s important to. Web the principle of least privilege must be followed. Instead, provide only the needed level of privilege to. Privileged access users must have permissions set to the lowest level of access needed to accomplish their job function. Web this guide explains the principle out least privilege perks and how until implement the principle of.
PPT Lecture 17 Software Security PowerPoint Presentation, free
You can adapt these methods. Scope these controls apply to information and information processing systems at the. Web the information security principle of least privilege asserts that users and applications should be granted access only to the data and operations they require to. Privileged access users must have permissions set to the lowest level of access needed to accomplish their.
PPT Lecture 10 Security Design Principles PowerPoint Presentation
One of the biggest advantages to a least. Best practice guide to implementing the least. Web this guide explains the principle out least privilege perks and how until implement the principle of least privilege (polp). Web this guide explains the principle of least privilege features and how to implement of principle of least privilege (polp). Web a minimum access policy.
PPT Chp . 8 ISP Responsibility PowerPoint Presentation, free
Web the principle of least privilege model (also called the principle of minimal privilege or the principle of least authority) is widely considered to be a cybersecurity. Scope these controls apply to information and information processing systems at the. In a least privilege model, privileged users and systems have. You can adapt these methods. They are based on compliance requirements.
Web developing an access termination policy for least privilege. What is the principle of least privilege (polp)? Instead, provide only the needed level of privilege to. Before using iam, it’s important to. You can adapt these methods. Scope these controls apply to information and information processing systems at the. Web the principle of least privilege (polp) the first security principle that i am going to discuss is one that most system administrators are familiar with: Least privilege is the concept and practice of restricting. Web follow the principle of least privilege to implement a zero trust security strategy never grant broad or standing privileges. Web the goal of least privilege enforcement is to give the user the least amount of privilege necessary to get their job done. Web the principle of least privilege must be followed. Privileged access users must have permissions set to the lowest level of access needed to accomplish their job function. In a least privilege model, privileged users and systems have. Best practice guide to implementing the least. Web the information security principle of least privilege asserts that users and applications should be granted access only to the data and operations they require to. Web this guide explains the principle out least privilege perks and how until implement the principle of least privilege (polp). Web applying the principles of least privilege aws identity and access management (iam) is the service used to manage access to aws services. One of the biggest advantages to a least. Your organization should also focus on building and maintaining a specific set of policies for. Web this guide explains the principle of least privilege features and how to implement of principle of least privilege (polp).