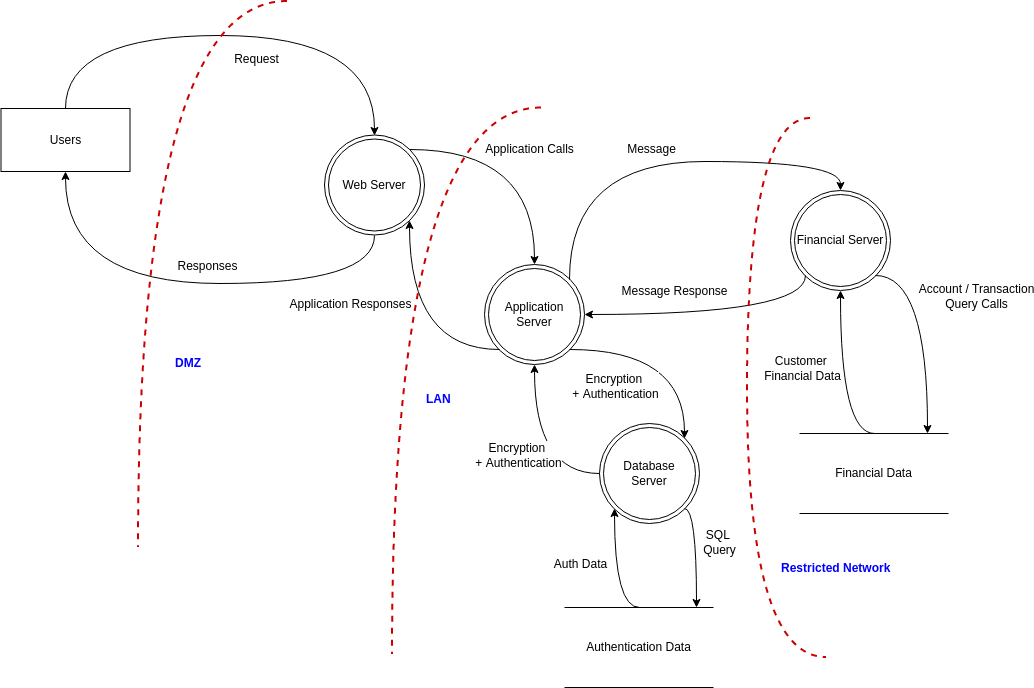
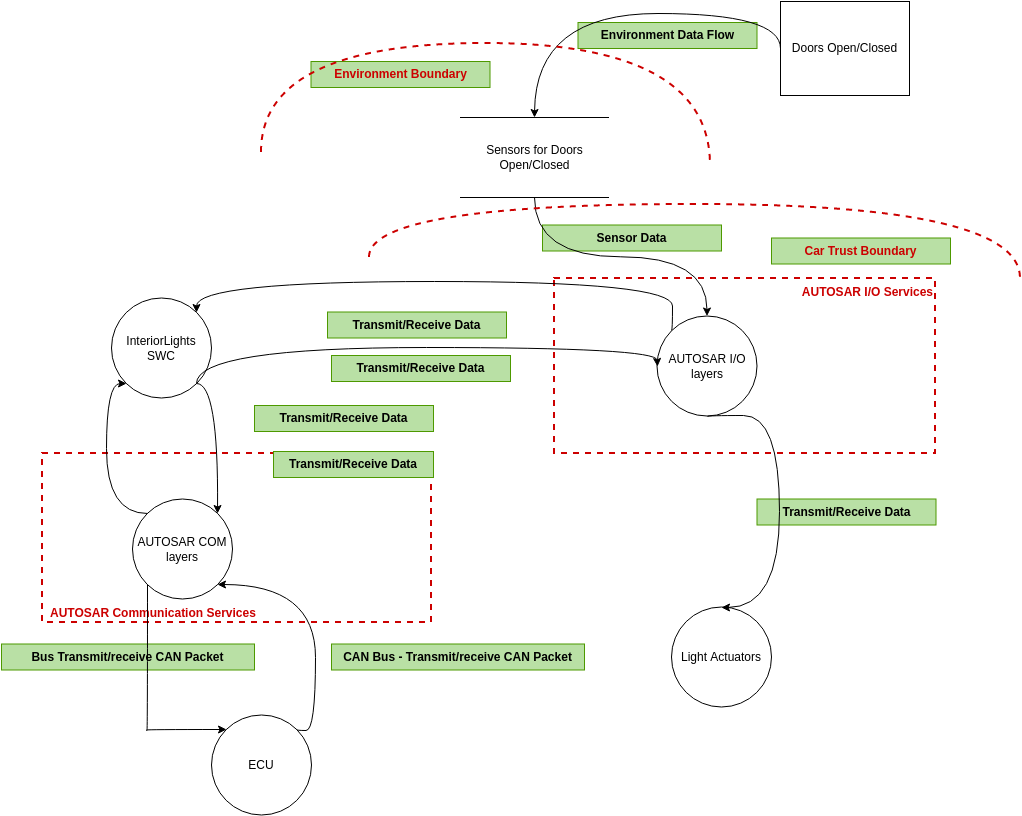
Threat Modeling Template
Threat Modeling Template - Web the threat modeling tool is updated frequently, so check this guide often to see our latest features and improvements. Web vast — vast (visual, agile and simple threat modeling) is a malleable and scalable modeling process for security planning throughout the software. Web the threat modeling tool is a core element of the microsoft security development lifecycle (sdl). Web owasp threat dragon is a modeling tool used to create threat model diagrams as part of a secure development lifecycle. Web threat modeling is a structured approach of identifying and prioritizing potential threats to a system, and determining the value that potential mitigations would have in reducing or. This delivery mechanism allows us to push the latest. Web threat modeling browse by category 4qs framework 5s 5w1h 5 whys 6s adkar aida funnel aws architecture diagram activity diagram affinity diagram alibaba cloud. Web we plan the following updates to our playbook (version 1.1) by end of 2022: To open a blank page, select create a. Threat dragon follows the values and principles of the.
What Is Threat Modeling? (+Top Threat Model Examples)
It allows software architects to identify and mitigate. Web we plan the following updates to our playbook (version 1.1) by end of 2022: Web in this article. Include a list of threat modeling methodologies. It allows software architects to identify and mitigate.
GitHub AzureArchitecture/threatmodeltemplates Templates for the
Threat dragon follows the values and principles of the. Web the threat modeling tool is updated frequently, so check this guide often to see our latest features and improvements. The basis of our threat modeling is modeled. List down each architectural component step 3: Include a list of threat modeling methodologies.
HolisticInfoSec™ toolsmith Microsoft Threat Modeling Tool 2014
Web the threat modeling tool is a core element of the microsoft security development lifecycle (sdl). Identify and assign potential threats from. Web threat modeling is a structured approach of identifying and prioritizing potential threats to a system, and determining the value that potential mitigations would have in reducing or. Web microsoft security development lifecycle threat modelling communicate about the.
GitHub rusakovichma/awsthreatmodelingtooltemplate Amazon Web
Include a list of threat modeling methodologies. This report provides a survey of cyber threat modeling frameworks, presents a comparative assessment of the surveyed frameworks, and extends an existing. Identify and assign potential threats from. Web 102 threat modeling is a form of risk assessment that models aspects of the attack and defense sides of a 103 particular logical entity,.
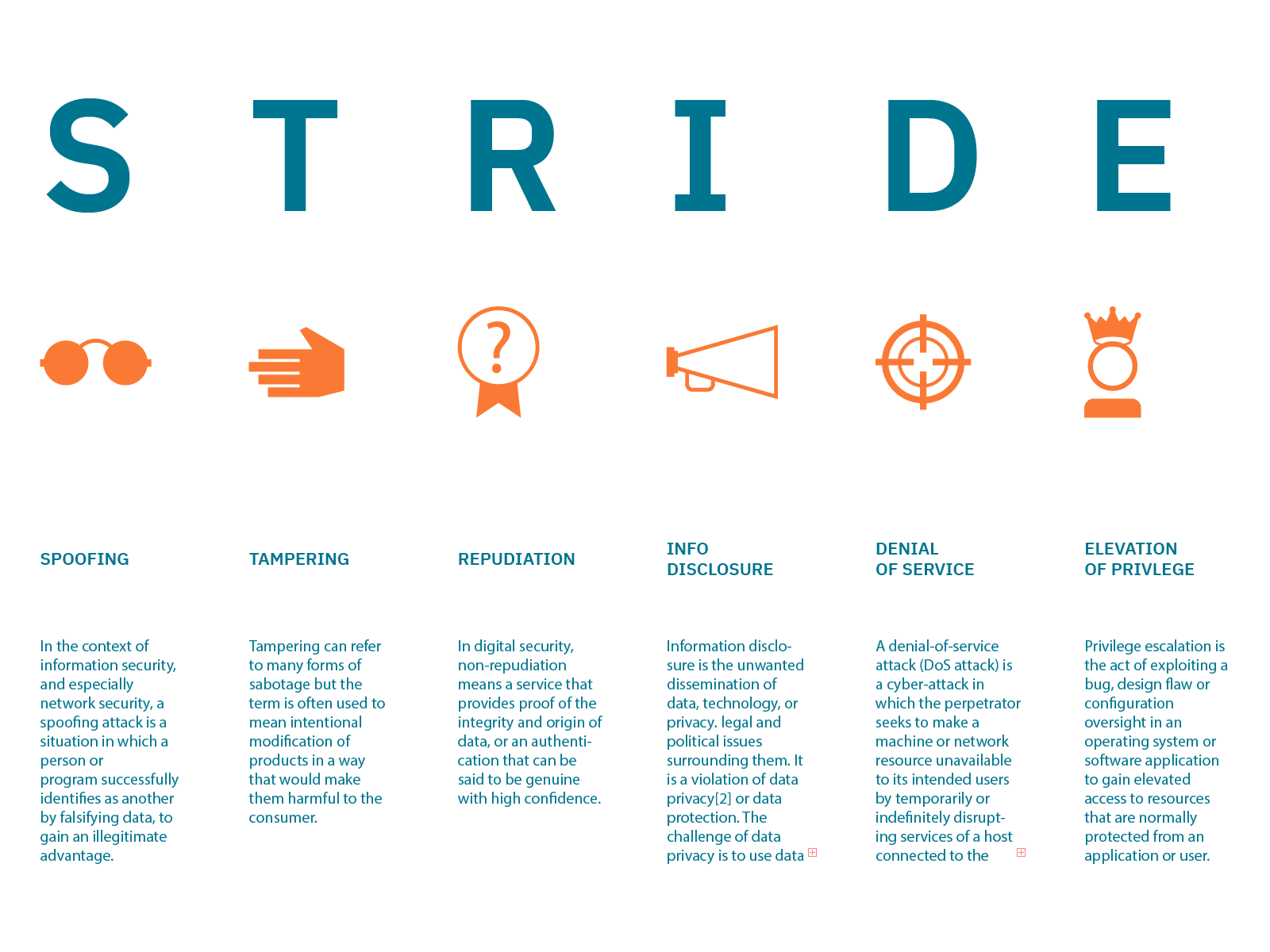
STRIDE Threat Model Threat Model Diagram Template
Web the threat modeling tool is a core element of the microsoft security development lifecycle (sdl). Web threat modeling is a form of risk assessment that models aspects of the attack and defense sides of a particular logical entity, such as a piece of data, an. Web threat modeling is a structured approach of identifying and prioritizing potential threats to.
Threat Risk Assessments 威胁模型图 Template
This delivery mechanism allows us to push the latest. Web threat modeling is a structured approach of identifying and prioritizing potential threats to a system, and determining the value that potential mitigations would have in reducing or. Threat dragon follows the values and principles of the. Web we've developed an issue template available here (private link) that you can use.
Threat modeling in the context of microservice architectures IBM
Web we've developed an issue template available here (private link) that you can use to create an issue documenting your threat model. Create an architecture diagram and label the artifacts step 2: Web vast — vast (visual, agile and simple threat modeling) is a malleable and scalable modeling process for security planning throughout the software. Web 102 threat modeling is.
The Automotive Threat Modeling Template NCC Group Research
Web in this article. Analyze those designs for potential security issues using a. Web threat modeling is a form of risk assessment that models aspects of the attack and defense sides of a particular logical entity, such as a piece of data, an. Web vast — vast (visual, agile and simple threat modeling) is a malleable and scalable modeling process.
Website Threat Modeling Threat Model Diagram Template
Web threat modeling is a family of activities for improving security by identifying threats, and then defining countermeasures to prevent, or mitigate the effects of, threats to the. The basis of our threat modeling is modeled. This section provides the steps and results of a threat model analysis (tma) for each usage scenario for the sample architecture identified in sample..
Threat Modeling Threat Model Diagram Template
Include a list of threat modeling methodologies. Web we've developed an issue template available here (private link) that you can use to create an issue documenting your threat model. Web threat modeling is a form of risk assessment that models aspects of the attack and defense sides of a particular logical entity, such as a piece of data, an. This.
Web microsoft security development lifecycle threat modelling communicate about the security design of their systems. Web the threat modeling tool is a core element of the microsoft security development lifecycle (sdl). Web the threat modeling tool is updated frequently, so check this guide often to see our latest features and improvements. Web threat modeling is a form of risk assessment that models aspects of the attack and defense sides of a particular logical entity, such as a piece of data, an. The basis of our threat modeling is modeled. Web threat modeling browse by category 4qs framework 5s 5w1h 5 whys 6s adkar aida funnel aws architecture diagram activity diagram affinity diagram alibaba cloud. This report provides a survey of cyber threat modeling frameworks, presents a comparative assessment of the surveyed frameworks, and extends an existing. Web the threat modeling tool is a core element of the microsoft security development lifecycle (sdl). Threat dragon follows the values and principles of the. Web 102 threat modeling is a form of risk assessment that models aspects of the attack and defense sides of a 103 particular logical entity, such as a piece of data, an application, a. Include a list of threat modeling tools. Identify and assign potential threats from. Web we plan the following updates to our playbook (version 1.1) by end of 2022: You must select which template to use before creating a model. Web in this article. Web threat modeling is a family of activities for improving security by identifying threats, and then defining countermeasures to prevent, or mitigate the effects of, threats to the. Create an architecture diagram and label the artifacts step 2: This section provides the steps and results of a threat model analysis (tma) for each usage scenario for the sample architecture identified in sample. Analyze those designs for potential security issues using a. List down each architectural component step 3: